Where Identity
Meets Security Trust Convenience Compliance Agility Integration Innovation Scalability Simplicity Versatility
Identity is the cornerstone of modern security. Secure your privileged assets and access with our unparalleled identity security backed by a zero-trust philosophy.







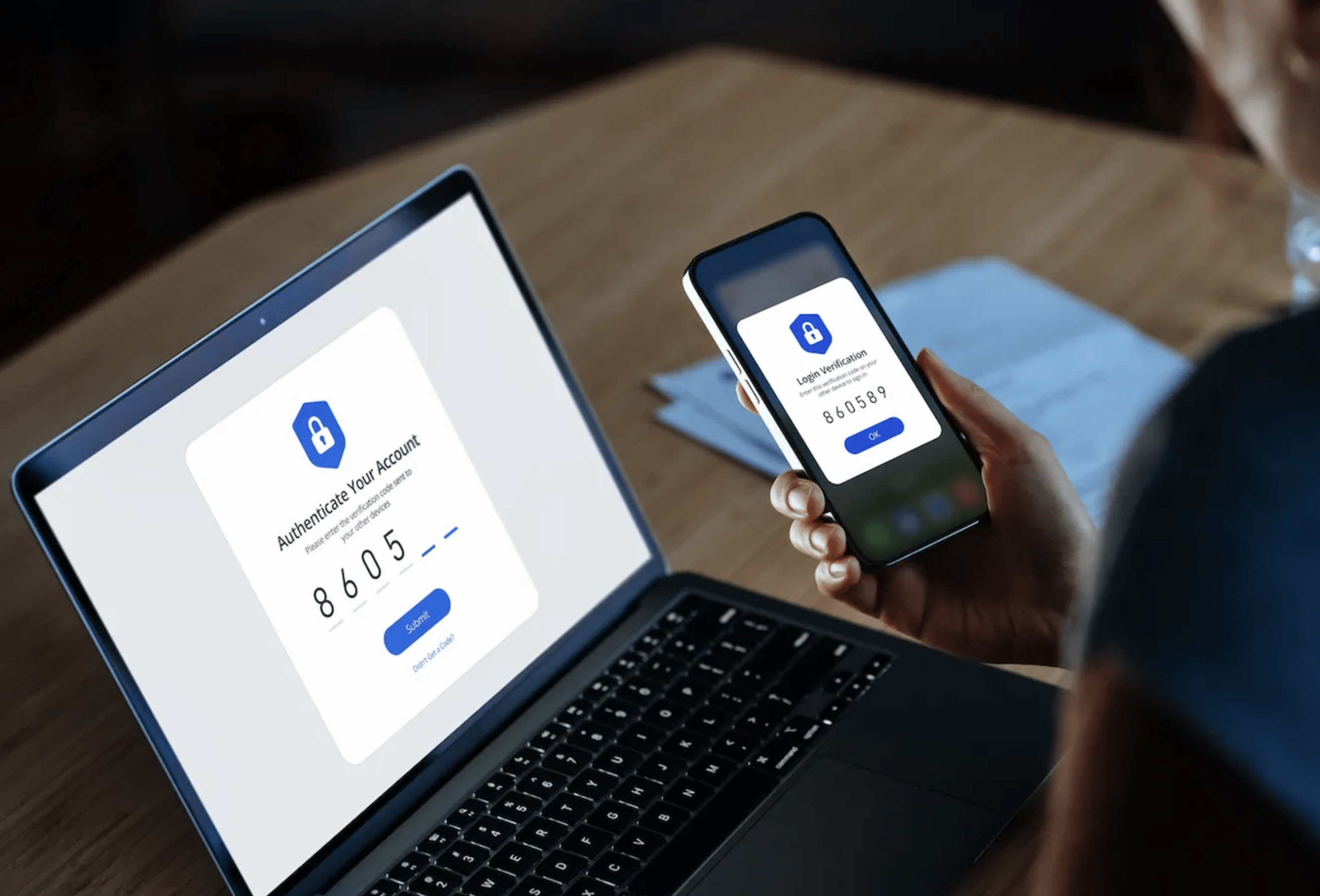
Elevate Your Identity Security Across All Fronts
Extend advanced identity protection beyond privileged users, encompassing a broad spectrum of digital identities and access requirements, for robust, dynamic security in every interaction.
Workforce Identity Security
Privileged Access Management
Endpoint Privilege Management
Secrets Management
Securing Tomorrow: Empowering Digital Identity Protection
Securing Tomorrow: Empowering Digital Identity Protection
What our clients are saying

“Deployment of Privileged Access Management (PAM) solution across enterprises has never been an easy feat. It takes an effort for the initial deployment, but the end result backed by exceptional support from SecureKi is worth it.”
Chia Nam Ling
CIO, Hap Seng Group
“SecureKi PAM reduces our operational overheads while providing the capability to define access rights on a need-to-know basis for all our users and helps us monitor their activities.”
Simon Cham
Former CIO, Malakoff Group
“For AVM Cloud, security is not just a necessity—it's a promise we make to our clients. SecureKi's Privileged Access Management solution integrates seamlessly into our cloud computing services, offering robust security measures that are easy to implement and manage. ”
Kenny Lim
CTO, AVM Cloud
“SecureKi's PAM solution has been a game-changer for AmBank. With its robust security features, we've strengthened our defense around SWIFT transactions, which is crucial for our banking operations. The deployment was fast and we've found the SecureKi service team to be knowledgeable and responsive, ensuring minimal downtime and high security. Their expertise in the financial sector has made SecureKi an invaluable partner for us.”
Nazri Seman
AmBank Security Operations, GCS
“Having a secure authentication and privileged access management in place for better control and visibility of our user access is a mandatory requirement under our Security Policy guidelines; we’re glad that SecureKi helped us to achieve this objective.”
Beh Swan Swan
Former CIO, Magnum Group
“GHL demands cutting-edge security for our payment services, and SecureKi has delivered a PAM solution that meets not only our compliance requirements but also the peculiarity of multiple on-prem and cloud data center setups. The forward-thinking privileged access management capabilities have been instrumental in streamlining our operations while bolstering our productivity in a secure manner.”
Tan Hong Sern
Group CTO, GHL Systems Group
“IPServerOne relies on SecureKi's PAM solution to manage and monitor privileged access across our diverse cloud hosting, backup, and storage services. The level of detail and control we now have is unparalleled, and SecureKi's real-time monitoring capabilities have been crucial in preempting potential security incidents. Their rapid deployment and outstanding support have made them a pivotal part of our security infrastructure.”
Cheung Loong Lee
Director, IP ServerOne Solutions











